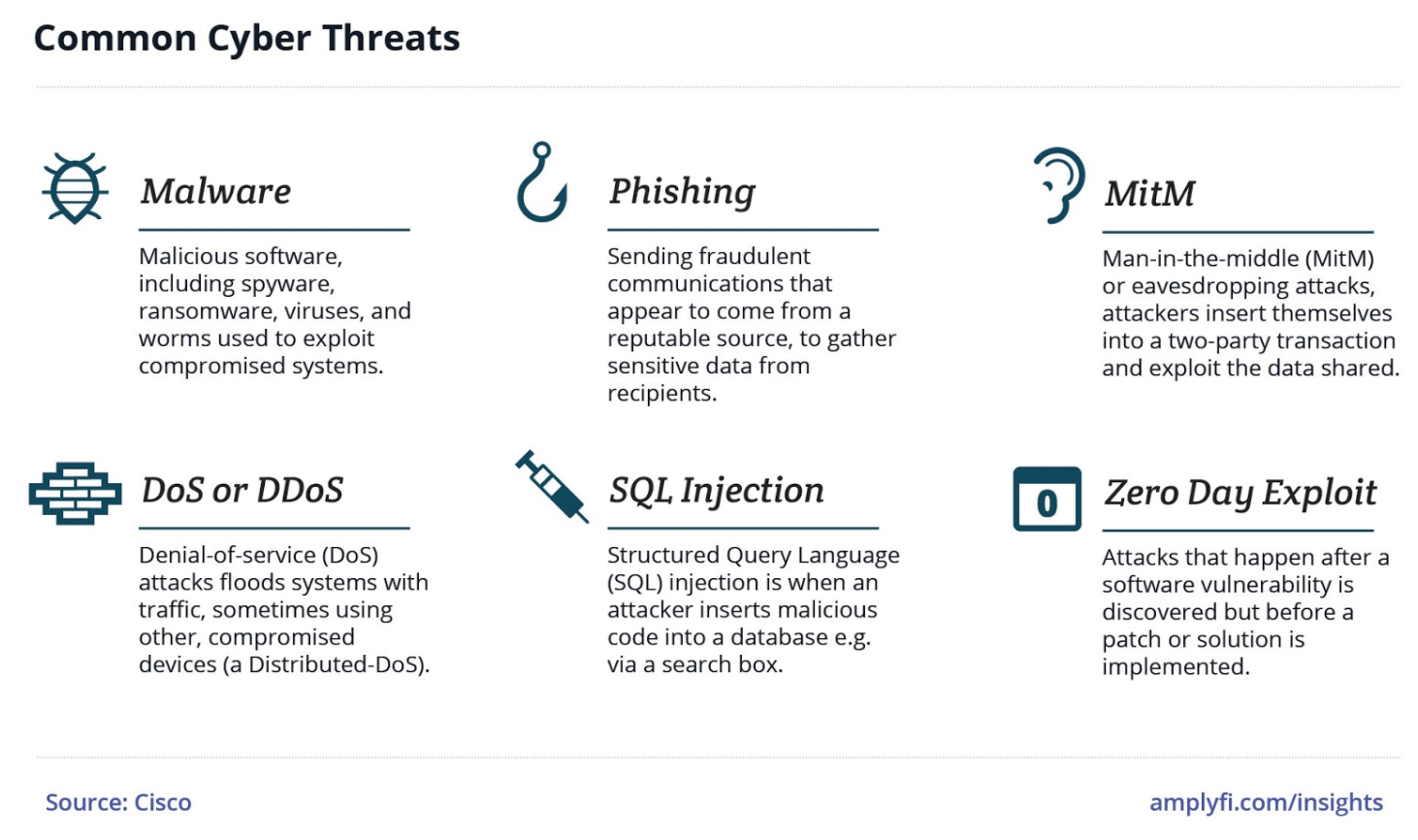
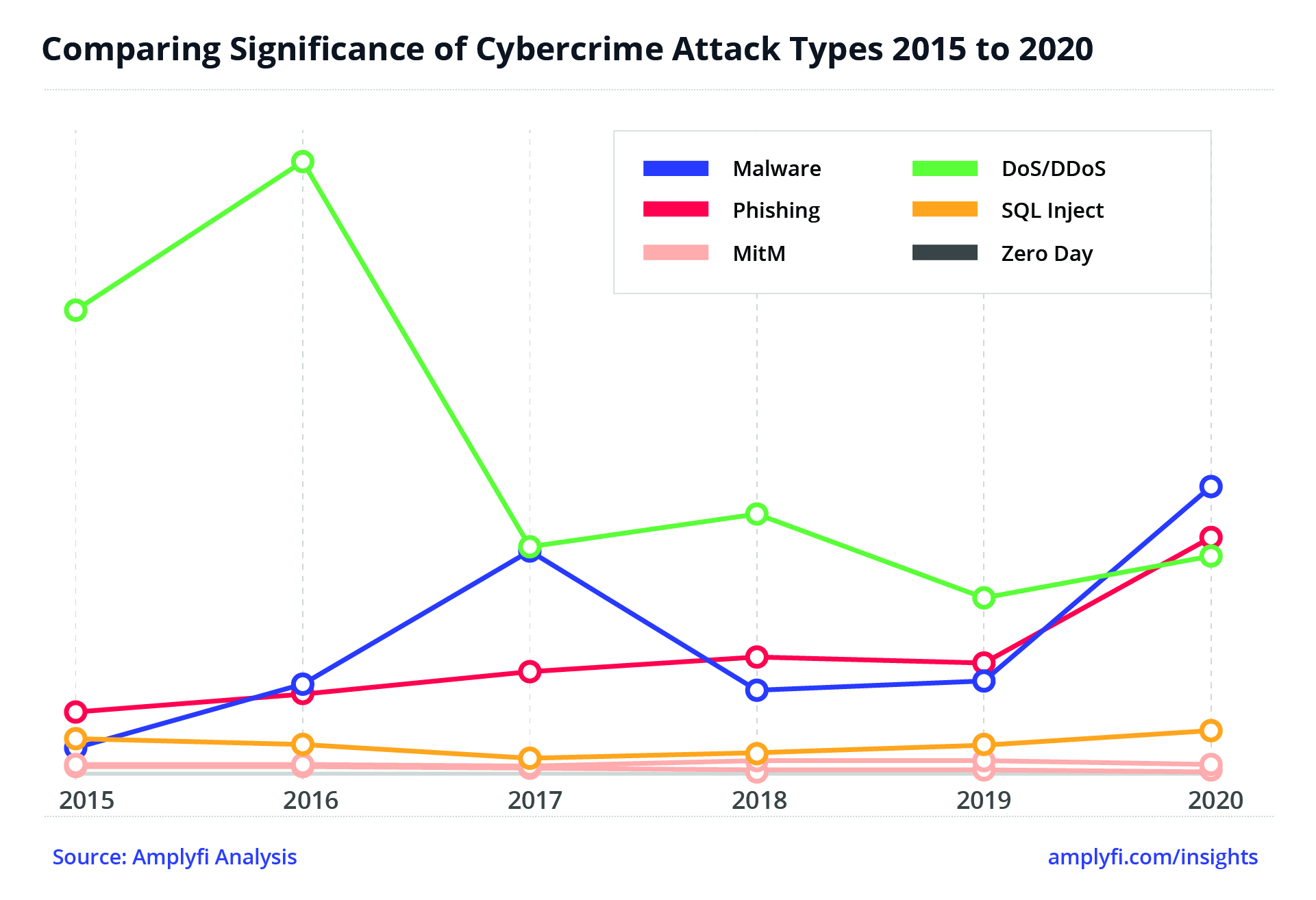
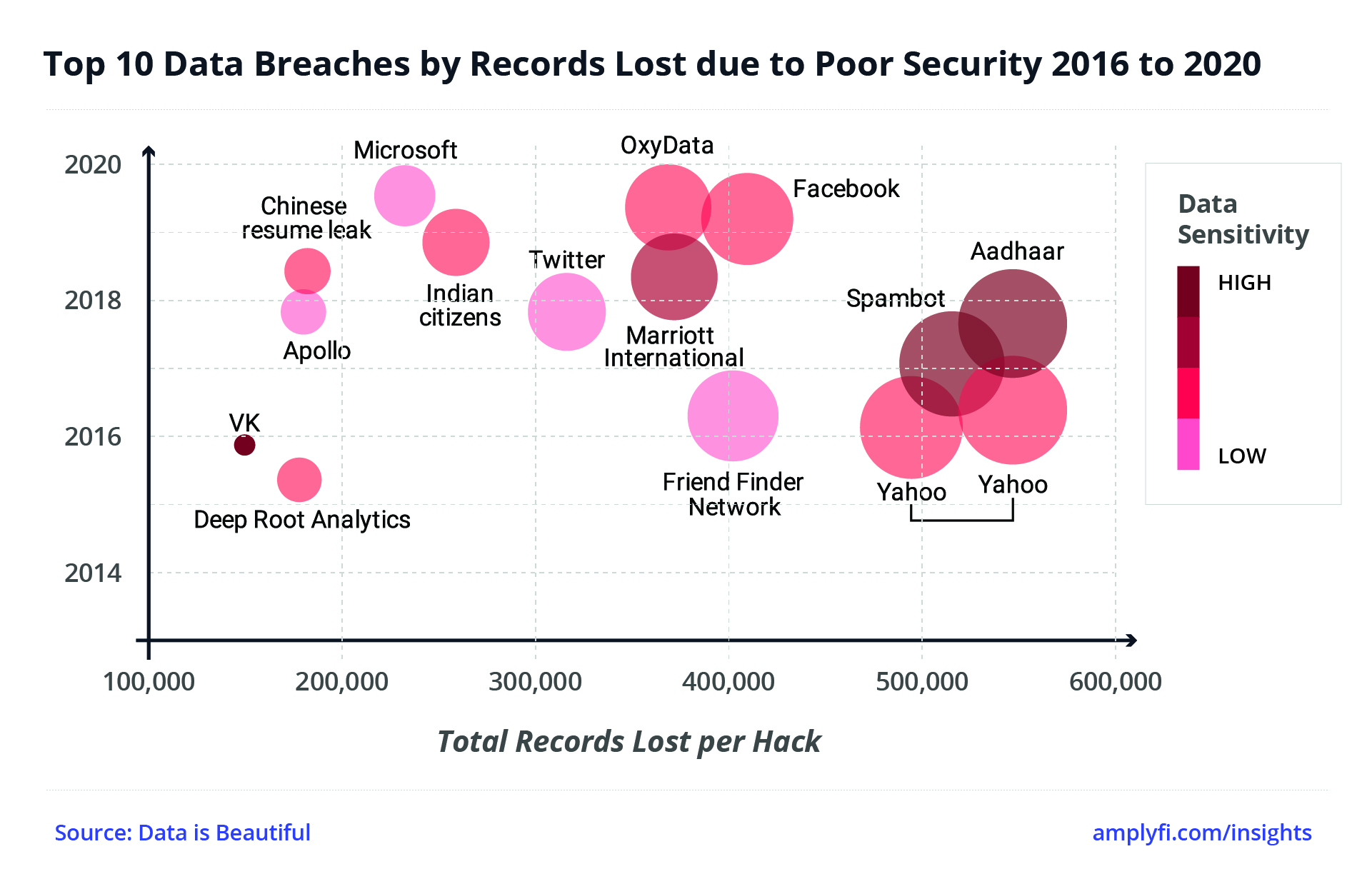
We mostly associate cybercrime with the loss of money, estimated to be a $1 trillion per year drag on the global economy and growing. But my biggest worry is not money. Cybercrime’s biggest threat is to our values and principles, the things money cannot buy.
Whether hacking accounts, stealing private data, or holding systems to ransom, financial loss is the standard measure of cybercrime. Awful though this is, cybercrime in this form does not undermine our society directly. Indeed, providing individuals take basic digital security precautions, then the likes of Mastercard and Visa will generally handle the losses. But what about democracy, a free press, or equality?
At AMPLYFI, we study the Deep Web. Away from the reach of consumer search engines it holds 95% of the internet’s data. However, the breeding ground for much cybercrime is the Dark Web. Here, unlisted, encrypted sites allow people to trade untraceable crypto-currencies for illicit goods or services. These activities are hard to track, quantify and control.
Our analysis of the Deep Web suggests that the next decade will be the most prolific ever for cybercriminals. The basis for our hypothesis is that cybercrime has emerged in lock-step with Digital Transformation. Put simply – the more value that goes online, the more attacks are leveraged there.
But the impacts are not confined to balance sheets and bank accounts. In a survey by McAfee (global computer security firm), 92% of respondents reported feeling effects from cybercrime that went beyond pure monetary losses. The lack of understanding of these “non-financial losses” is worrying in itself, but 56% of respondents also shared that they have no plan to prevent and respond to a cybersecurity incident. Until this metric moves, the impacts of cybercrime will inevitably increase.
Of growing concern is the loss of trust that results through stolen IP, fake news and destabilised democracies. A new Cold War is breeding a cabal of “digital arms dealers” whose “back-doors”, troll farms and ransomware are powering the geopolitical aspirations of shadowy non-governmental organisations.
Since medieval times, codes, cyphers and hidden messages have been used to influence global change. When communication went electronic, the solution became technical. During World War 2, at Bletchley Park in the UK, Alan Turing developed early mechanical machine-based technologies to break Germany’s “the unbreakable” Enigma code. Tommy Flowers, an engineer at the British General Post Office (GPO), then built Colossus, the first electronic programmable computer to decode the even more complex Lorenz code. The UK’s Government Communications Headquarters (GCHQ) the successor to Bletchley Park, went on to develop an early version of the now-ubiquitous “RSA asymmetric public key encryption” in the 1970s. In the mid-1990s military researchers in the US created “The Onion Router” (or Tor), which paved the way for the aforementioned Dark Web.
Gradually, a wave of state sponsored cyber-innovation spiralled out across the globe to Russia and China and more recently, in guerrilla form by groups such as the Islamic State. Much like the Cold War, that has extended into a conflict of values. Beyond finance and the state, to society itself, pitting Conservatives against Socialists, Brexiteers against Remainers, and now Vaxxers against Anti-Vaxxers. Suddenly nuclear submarines are not the hottest threat, when a troll farm can do so much more damage, with so little cost.
Whether stealing assets, disrupting processes or manipulating people, cybercrime is continually evolving. Digital innovations are being mutated into multi-nodal threats spanning everything from Whatsapp to Intel Microprocessors. As digital transforms more of our lives, these nodes are likely to multiply even further.
Added to this, the growing pressure for organisations to embrace the Digital Economy is irresistible. The early innovators, now far ahead in their Market Capitalisations, took risks that bought them time to develop and stress test systems. They have knowledge of the technical and social engineering dynamics of emerging attacks, including the constant weak link, humans. The Enigma code was ultimately breakable because of the human elements – people transmitted repetitive words that allowed codebreakers to build patterns faster.
Finance organisations have long known that security includes shaping customer behaviour, other sectors are learning this the hard way. User convenience is often the weak point, but how do we engineer secure systems that users can still access? Writing passwords down has long been an issue and current password managers and weak two-factor authentication systems are likely to cause many of our future issues or slow us down. If the single alpha-numeric password is now almost redundant, do we move to security keys based on images, feelings, or analogue data, such as physical properties? How else will we make the billions of Internet of Things (IoT) devices secure, or trust our driverless systems as they hurtle down our roads? Getting the balance right between convenience and security is clearly an area where the Financial Service sector can lead.
The onset of other technologies such as quantum computing will also cause disruptive ripples, as encryptions designed over the decades will be eclipsed by new emerging technologies just as Tommy Flowers’ computer showed. Ultimately, this is a race between legacy technologies and new ones But what can be done about it? Or, perhaps more pertinently, what will commercial organisations be allowed to do? Even when virtually unbreakable systems are possible, governments discourage them, fearing that it will enable criminals to exploit the anonymity provided. This is a bigger question for society – do we value more privacy or more security?
There are also societal questions when fast growing foreign organisations become critical to national infrastructure, such as Huawei in the EU and US. At scale, an extended disruption, with the cascading effect on national infrastructure could feasibly cause substantial disruption on the scale of other “Black Swan” events. If so, perhaps, a bit like the theft of money, we need to have systems able to accommodate the equivalent of someone breaking into the odd safe, providing the entire house of cards doesn’t collapse along with it.
Ultimately, at AMPLYFI, we believe it wise to assume that cybercrime is inevitable. Though assigning the resources to mitigate them can be a tough pill to swallow. As with many things digital, the experts are often not old enough to be in your boardroom, let alone take a role as Chief Information Security Officer (CISO). Indicating that sourcing experienced talent in this space is likely to become highly competitive.
Dealing with these potential disruptions will require a broad organisational view. Just as siloed “IT” morphed into Digital Teams and “Informatics” into Data Science, Information Security will need to transform to deal with this change. It will need a systematic approach to not just individual cyber threats but how they combine to combat multi-nodal threats. Every branch of an organisation will need to become aware of all forms of cybercrime and cybersecurity. Because if you can’t buy it, then someone will definitely be trying to steal it.
Originally published in The Fintech Times January 2021 edition, full version available here.